Uptime is a primary concern for both front- and back-end developers, but it’s crucial for all sorts of server-side admins, too. Unfortunately, one of the most effective ways for bad actors to ruin your site is to take it down using a Distributed Denial of Service (DDoS) attack and reduce its uptime. As such, most of you who work with websites will want to know how to stop a DDoS attack, or at least mitigate it.
This post will look at how to stop a DDoS attack. But before we get to the exact steps, let’s set the scene. To do that, we’ll first look at what a DDoS attack is and learn how to identify one.
What a DDoS attack is
In general terms, a regular (not distributed) Denial of Service (DoS) attack looks to overwhelm server resources to bring a site offline. A bad actor will use superfluous requests to disrupt the services of a host on a network with the result that legitimate requests can’t get to the site.
You can think of this like a protest outside a store. If people block the entrance to the building, customers can’t get in and, in effect, the store can’t trade optimally (or even at all.)
A DDoS (Distributed Denial of Service) attack uses many remote computers in a network to achieve this goal. It’s actually similar to the “Slashdot effect,” where legitimate, unprecedented traffic (often due to a link from a high-traffic website) can cause a site slowdown or crash. However, whereas this has a legitimate reason for being, a DDoS attack is always planned and malicious.
For instance, many of the machines a DDoS attack will use have suffered an exploit or malware injection. An attacker will control these “bots” using remote instructions to target a particular IP address, and each can look legitimate.
One of the key factors in a successful DoS attack is for the target to have slower internet speeds than the attacker. Modern computing technology makes this difficult, which is why DDoS attacks perform much better for the bad actor.
On the whole, the distributed nature of a DDoS attack makes it hard to identify an attack under typical circumstances.
How to identify a DDoS attack
If you want to learn how to stop a DDoS attack, you’ll need to understand what one looks like first. This can be difficult as there might be a legitimate reason for your high traffic numbers.
At a high level, if a site slows or crashes, this is a sign to implement your disaster plan (more of which later.) From there, you’ll want to look out for a number of telltale signs:
- Lots of traffic that all presents common signatures. This could mean that traffic emanates from the same IP address or range of addresses. In other cases, you might spot traffic coming from a similar location, referring website, or device type.
- There might also be a traffic surge to a single site endpoint – usually a particular page. Lots of 404 errors can be a clear sign, too.
- Traffic patterns that don’t align with what you’d expect your site to receive. For instance, this might be a peak outside of your usual time range or an unnatural event such as on-hour spikes in activity.
- Any and all of these could be legitimate rather than malicious. As such, you’ll want to lean on your analytics software to figure out what’s relevant and related.
You should also keep in mind that not all DDoS attacks are the same, and the different types can make this problem much more complex. Therefore, it’s important to be aware about these types if you want to know how to stop a DDoS attack.
The different types of DDoS attacks you’ll come across
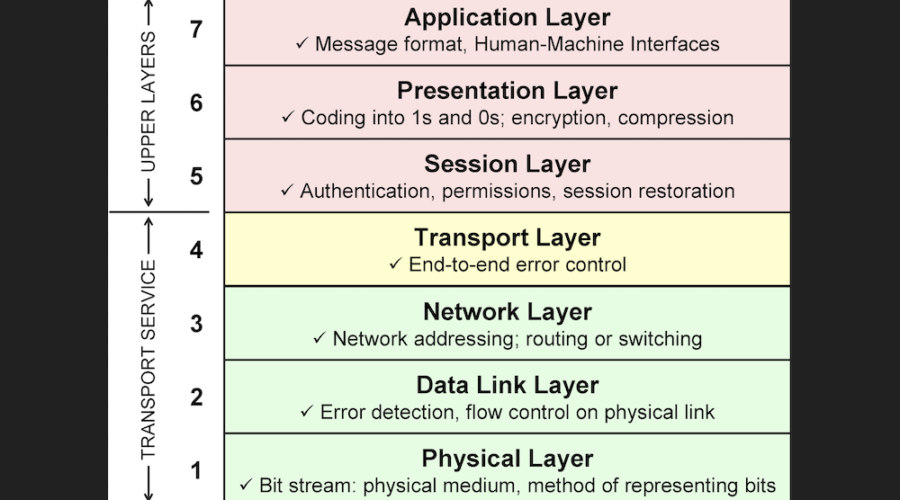
“Network connectivity” can seem like a simple phrase to describe the way computers link across the web, but that’s a fallacy. The Open Systems Interconnection (OSI) model shows the actual layered intricacies of network connections and communications systems:
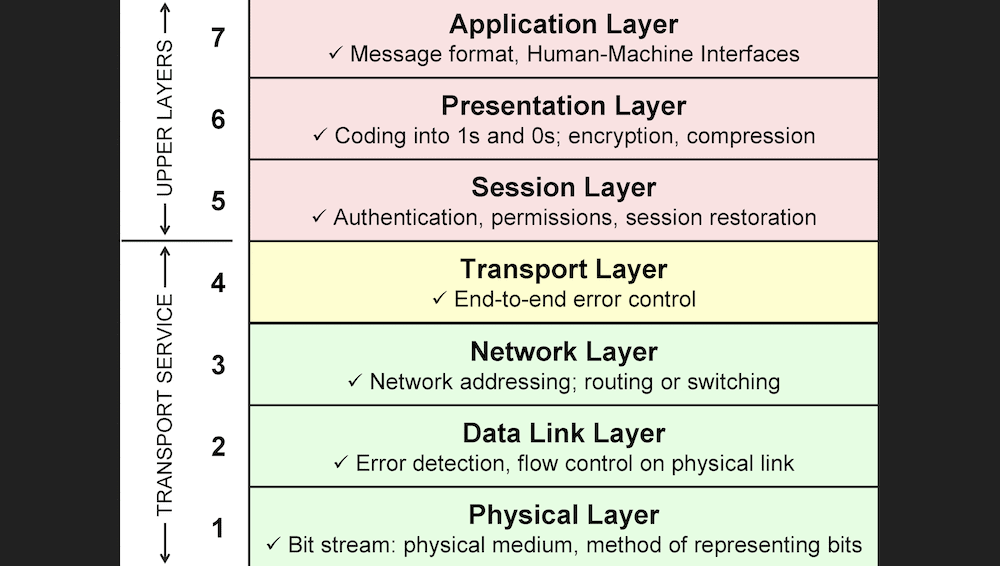
DDoS attacks fall into different categories based on which layer they target. Even so, you can bunch them into different groups. While you could do this on a per-layer basis, it’s also acceptable to classify them by what the DDoS attack targets.
For instance, volumetric attacks look to overwhelm the network and transport layers (three and four.) Attacks here can alter how the data moves across the web, and the effectiveness of the transmissions protocols.
One type – a Domain Name System (DNS) amplification attack – uses “botnets” to spoof the target IP address and make requests to an open DNS server. This causes the server to respond to the target IP and overwhelm the resources.
Protocol layer attacks
Protocol or infrastructure layer attacks also target layers three and four, and represent a typical way to conduct a DDoS attack. This is where the server’s resources and network equipment can’t handle the data coming in.
An example here is a User Datagram Protocol (UDP) reflection attack. This leverages the stateless nature of UDP. You can create a valid UDP request packet using almost any programming language. To carry out a successful attack, you’d only need to list the target’s IP address as the UDP source address.
The server this data heads to will amplify the data to create a bigger response packet, then reflect it back to the target IP address. As such, a bad actor doesn’t need to make a server connection at any point, which is cheap to produce.
When you connect to a web server, you’ll conduct a “three-way handshake” between client and server that involves both synchronization (SYN) and acknowledgement (ACK) packets. While the server sends a combined SYN-ACK packet, the client sends singular SYN and ACK packets.
With a SYN flood attack, the client – in this case the malicious user – sends multiple SYN packets, but doesn’t send the final ACK packet. This leaves lots of half-open Transmission Control Protocol (TCP) connections, which means the server runs out of capacity to accept new ones. It’s yet another way to keep available connections away from legitimate users.
Application layer attacks
You won’t only see DDoS attacks on the third and fourth layers. The application layer – number seven – is on the top level. This means it handles human-computer interactions and lets apps access network services.
As such, there are plenty of DDoS attacks that manipulate this layer, often using HTTP requests. For the client, a HTTP request is cheap, but for the server it’s expensive to respond to from a technical standpoint. Attacks can look like legitimate traffic, mainly because they use the same methods to access a site.
For instance, a HTTP flood is much like pressing the refresh button on your browser in a continuous cycle. Once this type of DoS interaction becomes a DDoS, it becomes more complex.
The style of the HTTP flood can also be complex, which will use many different IP addresses and random signatures to target a huge range of web URLs to expand the scope of the attack. Even a simple implementation that targets a single URL will cause lots of damage.
For a hacker, the Slowloris attack takes up less bandwidth but can cause more chaos. Here, each request takes an infinite amount of time to process for the server and monopolizes all the available connections. Because this attack is effective against servers with relatively available few concurrent connections, you’ll see this affect smaller websites often.
How to Prepare for a DDoS attack
Preparation is how to stop a DDoS attack, because the faster you can return to normal, the better. In fact, you likely can’t remove the threat in its entirety, but you can reduce the potential problems to a minimum.
Before that though, you will want to “tally up” how much you’re willing to spend, as cashflow can determine your plan of how to stop a DDoS attack. You should start from how much an attack will cost your business, then work back to determine the budget available to you. It’s not a calculation you’ll want to make mid-attack.
From there, you’ll want to note three key areas where you should focus on your preparation.
- Create a disaster and recovery plan, as this will tell everyone on your team what to do in explicit detail.
- From there, you can spend some of your budget allocation on a dedicated DDoS protection service. This will put experts in place to monitor sites, “bat away” some of the malicious traffic you receive, and more.
- Learn to spot when a DDoS attack will start. Your site analytics will be crucial here, as you can monitor for the telltale signs of a DDoS attack and react before something catastrophic happens.
On a technical level, there’s much more you can do to help stop a DDoS attack before it starts. We’ll cover this next.
How to Mitigate a DDoS attack
Since one of the biggest problems with how to stop a DDoS attack is the struggle to tell good traffic from bad, you can’t rely on one solution only to mitigate it. This is especially true if you look at “multi-vector” DDoS attack – i.e., those that attack multiple OSI layers.
As such, you’ll also want to layer your provision up to help your defenses. There are some simple ways to do this:
- Blackhole routing. This is where you filter traffic to a null route and drop it from the network. Without specific filtering, you’ll throw out all traffic, which won’t be ideal.
- Rate limiting. While this won’t be enough on its own to halt a DDoS attack, you can cap the number of actions completed by each user.
- Network diffusion. If you take the traffic hitting your site and scatter it across a distributed network, you’ll spread the impact of a DDoS attack in theory.
As such, scaling your bandwidth, network connections, and other resources are some of the best ways to combat a DDoS attack. Some of the solutions we’ll talk about later come as a cloud service, which distributes traffic as a defense.
You can also use on-site solutions, such as CAPTCHAs, to protect important endpoints on your site. This is where your login pages require a high-level of security, because you can place resource-heavy elements of your site behind login screens or other protective aspects.
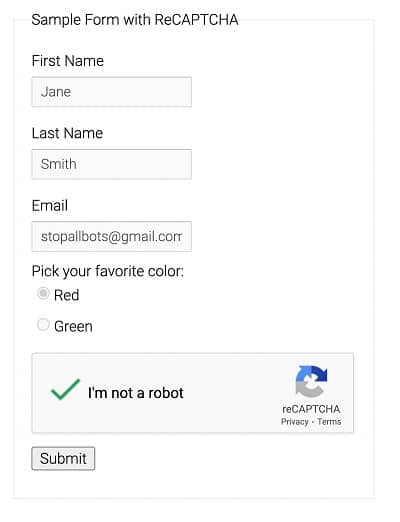
What’s more, you can implement some manual technical considerations. For example, you can set lower SYN or UDP thresholds, and time out half-open connections on the server.
A four-step strategy for how to stop a DDoS attack
Over the rest of this article, we’re going to show you how to stop a DDoS attack in four steps. The good news is that the advice we’ll give is not prescriptive and strict. As such, you can adapt the ideas to your own needs.
Here’s what we’ll cover:
- How a response plan and crisis strategy can save your bacon.
- What approach you should use to defend a web server.
- The benefits and drawbacks of on-premises DDoS protection.
- What cloud-based DDoS mitigation can do for you.
Let’s start with a topic we already mentioned – strategizing.
1. Formulate a strategy and response plan
It’s a fantastic idea to solidify everything you’re going to do in an official disaster and response plan. This should be one of the most detailed documents you have at your business, and include all the steps you’ll take to stop the attack and recover your resources.
Here are a few items of note to include:
- The steps each team member should follow, in order, when you respond to a DDoS attack.
- There should be instructions for those outside the team who have to communicate issues to customers, clients, suppliers, vendors, and any other interested party.
- You’ll want to include important contact details for your Internet Service Provider (ISP,) DDoS protection service, and others on the front line.
Once this is in place, the whole company will understand what it needs to do to protect your site’s server.
2. Figure out how to defend your web server
There are two primary issues with DDoS attacks:
- It’s hard to tell when an attack happens.
- If you have to react to an ongoing attack, it’s already too late.
To solve both of these problems, you’ll want to employ a DDoS protection service. Cloudflare is one of the best, and it includes dedicated server architecture on a global scale to intercept, spread, and filter web traffic accordingly.
With this in mind, you won’t want to implement static traffic thresholds or fill up your IP blocklist, as this won’t be enough, and is a reactive measure most times. Because scalability is one of the best ways of how to stop a DDoS attack, the “homespun” method has bandwidth constraints that dedicated services do better.
3. Implement on-premises protection
On-premises DDoS protection uses hardware devices on the network to filter out traffic for protected servers. This can be a viable and sophisticated way to mitigate and stop a DDoS attack.
Radware and F5 produce hardware DDoS mitigation units, and some also produce a hardware WAF (Web Application Firewall) too.
However, on-premises protection can only do so much, and won’t be able to stop a large-scale attack – especially a DDoS. As such, you’ll want to supplement with a cloud-based DDoS setup for the best response on how to stop a DDoS attack.
4. Consider a cloud-based DDoS solution
In reality, more sites rely on cloud protection as it’s scalable, always on, and cheaper than hardware. Maintenance costs are also low.
You’ll find some DDoS services that only work on the ISP level, but those that work within the cloud have greater scope for protection. Often, these services have massive networks of computers to distribute traffic to.
For instance, Amazon’s AWS Shield takes advantage of its network to carry out automatic detection and mitigation of a DDoS attack. What’s more, you can customize how the tool protects your server alongside the first-party WAF.
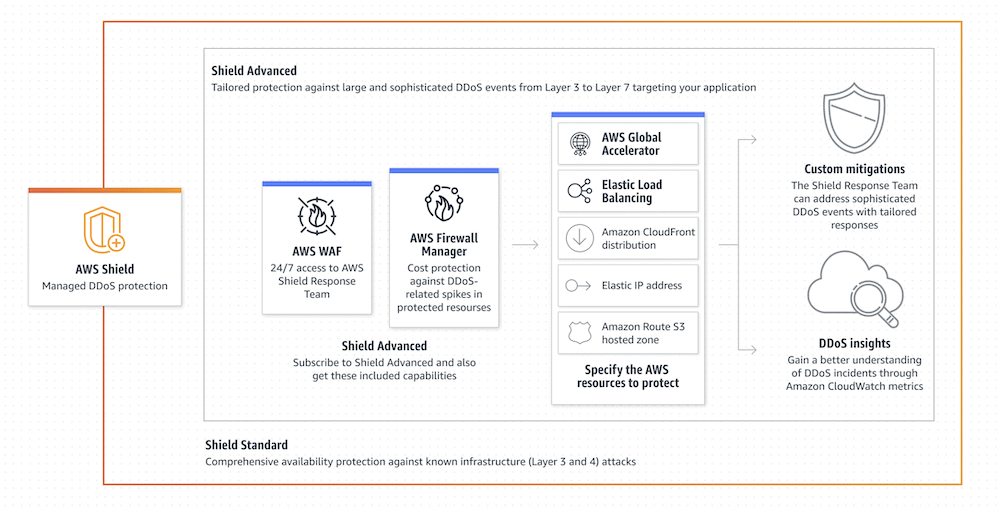
Cloudflare’s Magic Transit can perform well as a supplement to your existing on-premises solution. You’ll also get a full complement of tools to help you manage a virtual network, such as load balancers, advanced packet filtering, and more.
Conclusion 
A DDoS attack will see your site outgunned in the face of a malicious attempt to crash it. While it might seem defeatist, there’s no real way to stop any attack altogether, let alone DDoS attacks. As such, the answer for how to stop a DDoS attack is complex.
Mitigating the attack is a good strategy, and there’re plenty of implementations you can make at the server level. It’s important to figure out what your strategy is going to be, and how you want to defend your web server. On-premises protection is a fantastic idea, and a WAF is almost essential. Cloud solutions such as AWS Shield work, too, as well as on-site cloud standards such as CAPTCHAs.
Do you have any questions about how to stop a DDoS attack? Ask away in the comments section below!